This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
Connecting securely from MC to a Vertica database
When you use MC to monitor and manage a Vertica database, MC (running in a browser) connects as the client to the Vertica database server.
When you use MC to monitor and manage a Vertica database, MC (running in a browser) connects as the client to the Vertica database server.
MC uses JDBC for most database connections
MC uses Java Database Connectivity (JDBC) for most connections to a Vertica database, including:
-
Retrieving database information to display in charts
-
Running SQL queries through JDBC
-
Configuring and updating database properties
-
Configuring the database for extended monitoring
Exception
When MC uses Agents to perform AdminTools tasks, MC does not use JDBC to connect to the database.
Vertica software supports TLS
Vertica databases and Vertica MC support TLS up to version 1.2. This topic and its subtopics describe configuring TLS in MC for JDBC connections to a Vertica database.
MC requires that all certificate and key files for upload to MC must be in PEM (Privacy-enhanced Electronic Mail) format.
Vertica database security dictates how MC connects
The TLS/SSL security you configure for a database in MC must be consistent with the security configured on the database itself.
Whether the Vertica database has TLS/SSL configured in server mode or mutual mode, you should configure TLS/SSL for that database in MC to match.
To find out how a Vertica database is configured, see Determining the TLS mode of a Vertica database.
You can configure TLS/SSL in either server mode or mutual mode in MC.
The rest of this topic and related topics use the term TLS, TLS/SSL, and SSL interchangeably.
TLS server mode
When the MC client connects to a Vertica database configured in server mode:
-
The client requests and verifies the server's credentials.
-
The client does not need to present a client certificate and private key file to the server.
-
The MC administrator must configure the CA certificate that can verify server's certificate on MC when MC connects to the database over JDBC.
TLS mutual mode
When the MC client connects to a Vertica database configured in mutual mode:
-
The MC client requests and verifies the database server's credentials.
-
The server also requests and verifies the MC client's credentials.
-
Each MC user is a separate client, and must present a valid client certificate file and private key file pair (keypair), namely a certificate signed by a CA recognized by the Vertica database server as valid.
-
The MC administrator must configure:
-
The CA certificate to verify the Vertica database server certificate.
-
A client certificate and private key file (keypair) for each MC user. The keypair can be unique for each user, or shared by multiple users, depending on how client authentication is configured on the Vertica database. See Configuring client authentication.
-
Each MC user must be configured to map correctly to a user who is configured on the Vertica database server.
For more information on how Vertica supports TLS/SSL security, see TLS protocol.
Only MC users having Admin or Super privileges on a database are able to configure TLS certificates and keys on MC for database connections. The topics in this section use "MC administrator" to refer to both of these roles. For more information about MC user roles and privileges, see User administration in MC.
As the MC administrator, when you first configure security in MC for a Vertica database that requires mutual mode, you configure these certificates for the Vertica database:
-
The server certificate and public key of the database.
-
Your own client certificate and private key, as the first configured MC user mapped to a Vertica database user.
Configuring TLS/SSL on MC
MC provides the Certificates wizard for configuring TLS certificates for all JDBC connections to the database, to ensure those connections are secure.
In MC, there are three scenarios in which you need to configure TLS security for a Vertica database:
Adding certificates to MC for later use
You may want to add multiple CA certificates or client certificates to MC all at one time, to streamline the configuration of security when you are importing databases to MC or creating MC users. For details, see and .
To connect successfully, MC and database security must match
|
MC Security |
Vertica Database Security |
Does the connection succeed? |
|
None |
None |
Connection succeeds, and it is open and therefore unsecured. |
|
TLS server mode |
TLS server mode |
Connection succeeds provided MC can verify the server's certificate using the CA certificate configured on MC. |
|
TLS mutual mode |
TLS mutual mode |
Connection succeeds provided:
-
MC can verify the server's certificate using the CA certificate configured on MC.
-
The server can verify the client certificate and private key that MC presents as belonging to a mapped user on the Vertica database.
|
|
None |
TLS server mode |
MC attempts to establish an open connection. The connection fails if the Vertica database requires TLS for client connections. For more information, see:
|
|
None |
TLS mutual mode |
MC attempts to establish an open connection. The connection fails if the Vertica database requires TLS for client connections. The connection fails because MC does not present what the database requires: a valid client certificate and private key that the database can verify as belonging to a mapped database user. |
|
TLS server mode |
None |
MC attempts to connect to the database securely, however the connection fails as the database is not configured with TLS certificates. |
|
TLS mutual mode |
None |
MC attempts to connect to the database securely, however the connection fails as the database is not configured with TLS certificates. |
1 - Management Console security
The Management Console (MC) manages multiple Vertica clusters, all of which might have different levels and types of security, such as user names and passwords and LDAP authentication.
The Management Console (MC) manages multiple Vertica clusters, all of which might have different levels and types of security, such as user names and passwords and LDAP authentication. You can also manage MC users who have varying levels of access across these components.
Open authorization and SSL
Management Console (MC) uses a combination of OAuth (Open Authorization), Secure Socket Layer (SSL), and locally-encrypted passwords to secure HTTPS requests between a user's browser and MC, and between MC and the agents. Authentication occurs through MC and between agents within the cluster. Agents also authenticate and authorize jobs.
The MC configuration process sets up SSL automatically, but you must have the openssl package installed on your Linux environment first.
See the following topics for more information:
User authentication and access
MC provides two user authentication methods, LDAP or MC. You can use only one method at a time. For example, if you chose LDAP, all MC users will be authenticated against your organization's LDAP server.
You set up LDAP authentication up through MC Settings > Authentication on the MC interface.
Note
MC uses LDAP data for authentication purposes only. It does not modify user information in the LDAP repository.
The MC authentication method stores MC user information internally and encrypts passwords. These MC users are not system (Linux) users. They are accounts that have access to MC and, optionally, to one or more MC-managed Vertica databases through the MC interface.
Management Console also has rules for what users can see when they sign in to MC from a client browser. These rules are governed by access levels, each of which is made up of a set of roles.
See also
2 - Determining the TLS mode of a Vertica database
When you configure Vertica for TLS through the Management Console, you must configure the security mode to match what the Vertica database is configured to require: server mode or mutual mode.
When you configure Vertica for TLS through the Management Console, you must configure the security mode to match what the Vertica database is configured to require: server mode or mutual mode.
To determine the TLS mode for existing sessions, query the SESSIONS system table:
=> SELECT session_id, user_name, ssl_state FROM sessions;
session_id | user_name | ssl_state
---------------------------------+-----------+-----------
v_vmart_node0001-333611:0x1ab | dbadmin | mutual
To determine the Vertica database's client-server TLS configuration, query the TLS_CONFIGURATIONS system table for the "server":
=> SELECT name, certificate, ca_certificates, mode FROM tls_configurations WHERE name = 'server';
name | certificate | ca_certificates | mode
--------+------------------+---------------------+-----------
server | server_cert | ca_cert,ica_cert | VERIFY_CA
(1 row)
The "mode" can be one of the following, in ascending security:
-
DISABLE: Disables TLS. All other options for this parameter enable TLS.
-
ENABLE: Enables TLS. Vertica does not check client certificates.
-
TRY_VERIFY: Establishes a TLS connection if one of the following is true:
If the other host presents an invalid certificate, the connection will use plaintext.
-
VERIFY_CA: Connection succeeds if Vertica verifies that the other host's certificate is from a trusted CA. If the other host does not present a certificate, the connection uses plaintext.
-
VERIFY_FULL: Connection succeeds if Vertica verifies that the other host's certificate is from a trusted CA and the certificate's cn (Common Name) or subjectAltName attribute matches the hostname or IP address of the other host.
Note that for client certificates, cn is used for the username, so subjectAltName must match the hostname or IP address of the other host.
Mutual mode corresponds to TRY_VERIFY or higher, which indicates that Vertica is in mutual mode. In mutual mode, Vertica sends its server certificate to the client for verification, and uses the CA certificates (in this case, "ca_cert" and "ica_cert") to verify client certificates.
In contrast, a server mode configuration (which doesn't verify client certificates) might have the following TLS configuration instead:
=> SELECT name, certificate, ca_certificates, mode FROM tls_configurations WHERE name = 'server';
name | certificate | ca_certificates | mode
--------+------------------+---------------------+-----------
server | server_cert | | ENABLE
(1 row)
3 - Configuring TLS while importing a database on MC
To configure TLS as you are importing an existing Vertica database on MC:.
To configure TLS as you are importing an existing Vertica database on MC:
-
Follow the steps in Importing an existing database into MC.
-
In the Import Vertica window, select the database and click the Use TLS checkbox.
-
Click Configure TLS and Import DB to launch and complete the Certificates wizard.
MC certificates wizard
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server. Each screen presents options. When you select an option, the wizard displays additional options and details.
-
The first wizard screen provides helpful overview information. Read it, and click Configure TLS Certificates to continue.
-
On the Configure CA Certificates screen, configure a CA certificate (public key) to add to MC. MC uses this trusted certificate to verify the server's identity during TLS communications over JDBC connections between MC and the Vertica database server.
Complete one of these options:
-
Upload a new CA certificate Browse and select the certificate file and enter an alias for this certificate
-
To add another CA certificate, click Add More CA Certificates.
-
Continue adding additional CA certificates until you are finished.
-
Choose a certificate alias from previously uploaded certificates Select the alias for the previously uploaded CA certificate you wish to configure for the current database.
-
When you are done adding CA certificates, click Next.
-
The Configure Client Certificate screen displays the check box Add Client Certificate and Private Key for Mutual Mode TLS Connection.
-
If the database is configured for server mode, you do not need a client certificate or key.
-
If the database is configured for mutual mode:
-
Complete the detail fields for the client certificate and private key option you have chosen above, then click Next.
-
The Apply TLS configuration to MC users mapped to database window allows you to configure the client certificate-key pair you have just entered, for use by multiple MC users.
Note
All the MC users you select must be mapped to the same user id on the Vertica database server.
-
Click Review. The wizard displays a review window with the TLS options you have configured.
-
Select one of these options:
-
To modify your TLS choices, click Back.
-
To confirm your choices:
-
If you are importing a database, click Configure TLS and Import DB.
-
If you are configuring TLS for a database already imported to MC, click Configure TLS for DB.
-
Click Close to complete the wizard.
-
To close the wizard without importing the database and without setting up TLS configuration, click Cancel.
4 - MC certificates wizard
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server.
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server. Each screen presents options. When you select an option, the wizard displays additional options and details.
-
The first wizard screen provides helpful overview information. Read it, and click Configure TLS Certificates to continue.
-
On the Configure CA Certificates screen, configure a CA certificate (public key) to add to MC. MC uses this trusted certificate to verify the server's identity during TLS communications over JDBC connections between MC and the Vertica database server.
Complete one of these options:
-
Upload a new CA certificate Browse and select the certificate file and enter an alias for this certificate
-
To add another CA certificate, click Add More CA Certificates.
-
Continue adding additional CA certificates until you are finished.
-
Choose a certificate alias from previously uploaded certificates Select the alias for the previously uploaded CA certificate you wish to configure for the current database.
-
When you are done adding CA certificates, click Next.
-
The Configure Client Certificate screen displays the check box Add Client Certificate and Private Key for Mutual Mode TLS Connection.
-
If the database is configured for server mode, you do not need a client certificate or key.
-
If the database is configured for mutual mode:
-
Complete the detail fields for the client certificate and private key option you have chosen above, then click Next.
-
The Apply TLS configuration to MC users mapped to database window allows you to configure the client certificate-key pair you have just entered, for use by multiple MC users.
Note
All the MC users you select must be mapped to the same user id on the Vertica database server.
-
Click Review. The wizard displays a review window with the TLS options you have configured.
-
Select one of these options:
-
To modify your TLS choices, click Back.
-
To confirm your choices:
-
If you are importing a database, click Configure TLS and Import DB.
-
If you are configuring TLS for a database already imported to MC, click Configure TLS for DB.
-
Click Close to complete the wizard.
-
To close the wizard without importing the database and without setting up TLS configuration, click Cancel.
5 - Configuring TLS for a monitored database in MC
This procedure describes how to configure TLS for all JDBC connections to a database that is already being monitored in MC.
This procedure describes how to configure TLS for all JDBC connections to a database that is already being monitored in MC. Note that the Vertica database should already be configured with the TLS certificates required for TLS connections.
-
In MC, navigate to Databases and Clusters > DB-name > Settings and click the Security tab in the left navigation bar.
-
In the Configure TLS Connection for Database section, click Enabled in the drop-down beside Use TLS Connection to database.
-
Click Configure TLS Connection to launch and complete the Certificates wizard.
MC certificates wizard
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server. Each screen presents options. When you select an option, the wizard displays additional options and details.
-
The first wizard screen provides helpful overview information. Read it, and click Configure TLS Certificates to continue.
-
On the Configure CA Certificates screen, configure a CA certificate (public key) to add to MC. MC uses this trusted certificate to verify the server's identity during TLS communications over JDBC connections between MC and the Vertica database server.
Complete one of these options:
-
Upload a new CA certificate Browse and select the certificate file and enter an alias for this certificate
-
To add another CA certificate, click Add More CA Certificates.
-
Continue adding additional CA certificates until you are finished.
-
Choose a certificate alias from previously uploaded certificates Select the alias for the previously uploaded CA certificate you wish to configure for the current database.
-
When you are done adding CA certificates, click Next.
-
The Configure Client Certificate screen displays the check box Add Client Certificate and Private Key for Mutual Mode TLS Connection.
-
If the database is configured for server mode, you do not need a client certificate or key.
-
If the database is configured for mutual mode:
-
Complete the detail fields for the client certificate and private key option you have chosen above, then click Next.
-
The Apply TLS configuration to MC users mapped to database window allows you to configure the client certificate-key pair you have just entered, for use by multiple MC users.
Note
All the MC users you select must be mapped to the same user id on the Vertica database server.
-
Click Review. The wizard displays a review window with the TLS options you have configured.
-
Select one of these options:
-
To modify your TLS choices, click Back.
-
To confirm your choices:
-
If you are importing a database, click Configure TLS and Import DB.
-
If you are configuring TLS for a database already imported to MC, click Configure TLS for DB.
-
Click Close to complete the wizard.
-
To close the wizard without importing the database and without setting up TLS configuration, click Cancel.
6 - Configuring mutual TLS for MC users
You can configure TLS for existing MC users who are already mapped to Vertica database user ids.
You can configure TLS for existing MC users who are already mapped to Vertica database user ids. You would do so if you had just configured TLS in mutual mode on a previously unsecured Vertica database, and needed to configure a client certificate and private key for each MC user who accesses that database.
-
In MC, navigate to MC Settings and click the User Management tab.
-
Select a user from the list and click Edit.
-
In the Add permissions window:
-
Choose the database for which you want to edit this MC user's security permissions.
-
MC displays the database username to which this MC user is currently mapped.
-
In the Restrict Access drop-down, choose Admin, Associate, IT, or User to specify the privilege level for this user.
-
In the Use TLS Connection drop-down, choose Yes.
-
Click Configure TLS for user to launch and complete the Certificates wizard.
MC certificates wizard
The MC Certificates wizard lets you configure a CA certificate for the Vertica database server and client certificates for MC to allow secure TLS communication over the JDBC connections between MC and the Vertica database server. Each screen presents options. When you select an option, the wizard displays additional options and details.
-
The first wizard screen provides helpful overview information. Read it, and click Configure TLS Certificates to continue.
-
On the Configure CA Certificates screen, configure a CA certificate (public key) to add to MC. MC uses this trusted certificate to verify the server's identity during TLS communications over JDBC connections between MC and the Vertica database server.
Complete one of these options:
-
Upload a new CA certificate Browse and select the certificate file and enter an alias for this certificate
-
To add another CA certificate, click Add More CA Certificates.
-
Continue adding additional CA certificates until you are finished.
-
Choose a certificate alias from previously uploaded certificates Select the alias for the previously uploaded CA certificate you wish to configure for the current database.
-
When you are done adding CA certificates, click Next.
-
The Configure Client Certificate screen displays the check box Add Client Certificate and Private Key for Mutual Mode TLS Connection.
-
If the database is configured for server mode, you do not need a client certificate or key.
-
If the database is configured for mutual mode:
-
Complete the detail fields for the client certificate and private key option you have chosen above, then click Next.
-
The Apply TLS configuration to MC users mapped to database window allows you to configure the client certificate-key pair you have just entered, for use by multiple MC users.
Note
All the MC users you select must be mapped to the same user id on the Vertica database server.
-
Click Review. The wizard displays a review window with the TLS options you have configured.
-
Select one of these options:
-
To modify your TLS choices, click Back.
-
To confirm your choices:
-
If you are importing a database, click Configure TLS and Import DB.
-
If you are configuring TLS for a database already imported to MC, click Configure TLS for DB.
-
Click Close to complete the wizard.
-
To close the wizard without importing the database and without setting up TLS configuration, click Cancel.
7 - Updating TLS security for MC connections
Maintaining TLS security for MC JDBC connections to a Vertica database is an ongoing process.
Maintaining TLS security for MC JDBC connections to a Vertica database is an ongoing process. Initially, you as the MC administrator must configure the appropriate certificates and keys. As time passes, certificates expire or otherwise become invalid. To maintain TLS security in MC, you must configure new certificates to replace any that are about to expire.
If any of the certificates that secure an MC connection to a Vertica database changes or expires, the MC administrator must update the TLS configuration for that database on MC to ensure that unexpired certificates are available so that connections can succeed.
MC flags the current certificate for a given connection with a "use me" bit. This bit is set only for the current certificate. When you configure a new certificate for a given connection, the new certificate is marked current, and the previous certificate (although still present in the trust store or keystore) is no longer marked as the current certificate.
8 - Enabling or disabling TLS for a database in MC
To enable TLS for all JDBC connections from MC to a Vertica database, configure the certificate and key appropriate for that connection.
To enable TLS for all JDBC connections from MC to a Vertica database, configure the certificate and key appropriate for that connection. See:
Disabling a TLS connection
Under some conditions, you as the system administrator might need to disable TLS for JDBC connections from MC to a Vertica database. Here are some examples:
-
The TLS certificates are expired and you have not yet obtained new certificates.
-
The TLS certificates and keys are revoked and the user does not have new certificates and keys, but you still want to allow that user to connect from MC to the database to show monitoring information and run queries.
To disable TLS for connecting to a Vertica database:
-
In MC, navigate to Home > Databases and Clusters > DatabaseName > Settings.
-
Click the Security tab in the left navigation bar.
-
In the Use TLS Connection to database drop-down, choose Disabled.
Note
To reenable TLS for a database connection after you disable it, you must reconfigure the necessary certificates.
Disabling TLS for a database removes the configuration that tells MC to use the current certificates and keys for a given database, for all users. If it is a mutual mode TLS connection and each user had a separate client certificate and private key configured for that database, to re-enable TLS you must reconfigure the certificate and key for each user individually, for that database.
Re-enabling a disabled TLS connection
-
In MC, navigate to Home > Databases and Clusters > DatabaseName > Settings.
-
Click the Security tab in the left navigation bar.
-
In the Use TLS Connection to database drop-down, choose Enabled.
-
MC displays Configure MC to use secured connection to query Vertica database or modify existing configuration.
-
To finish re-enabling TLS, click Configure TLS Connection to launch the Certificates Wizard.
-
Complete the MC certificates wizard.
9 - Adding TLS certificates in MC
You can add one or more certificates to MC for later use, without immediately associating the certificates with a database.
You can add one or more certificates to MC for later use, without immediately associating the certificates with a database. Adding certificates ahead of time makes it easier to configure security for a database or for one or more MC users, because you can just choose a CA or client certificate from a list rather than having to add it to MC during the configuration steps.
Adding CA certificates in MC
To add one or more CA certificates in MC:
-
From the MC home page, navigate to MC Settings > SSL/TLS Certificates.
-
Under Manage TLS Certificates for Database Connection, click Add New CA Certificate.
-
In the Add new CA certificates for TLS connection window, enter an alias for the certificate, to make it easier to refer to later.
-
Click Browse to locate the certficate file you want to add. MC opens an Explorer window.
-
Select the file you want to upload, and click Open.
Note
Make sure the certificate file is unexpired, and is not protected by a password.
-
To add just this one certificate, click Add New CA. MC adds the certificate to its list.
-
To add additional CA certificates, click Add More CA Certificates. MC adds the certificate to a list, and clears the fields so you can enter the next CA certificate.
-
Repeat the process until you have entered the last certificate you want to add.
-
Click Add New CA to add all the CA certificates in the list to the MC:
Adding client certificates and keys in MC
You can add one or more client certificate and private key pairs to MC. In each pair, you can add either a single certificate, a preexisting certificate chain, or a series of client certificates that MC uses to create a new certificate chain.
To add one or more client certificates with their private key files to MC for later use:
-
Navigate to Home > MC Settings > SSL/TLS Certificates.
-
Under Manage TLS Certificates for Database Connection, click Add New Client Certificate. MC displays the Add new Client Certificate and Private Key for TLS Connection screen.
Note
When you add a client certificate to MC, you always add it with its private key file. The client certificate and its key are a key pair.
-
Click one of these file upload options:
- Upload Client Certificate and Private Key for TLS Connection. With this option, you paste a certificate and key into browser fields. MC posts the certificate and key from your browser to the MC server via an https connection over the network, secured with TLS/SSL.
- Manually upload Client Certificate and Private Key on MC host and provide paths. Sending the certificates from your browser to the MC server across an https network connection may not be not your preference. If so, you can use this option to specify the paths on the MC server host where you have manually uploaded the client certificate and private key files, instead. The URL of your MC browser shows the IP address of the MC host. Using this option, you must manually handle the transfer of the certificate and the key files to the server.
-
To provide a single client certificate and private key with either input option:
-
Enter a recognizable alias for the key pair.
-
Browse and select the private key file or provide the path.
-
Browse and select the client certificate file or provide the path.
-
Click Add New Client Certificate.
-
MC adds the key pair to its list.
-
To upload several certificates and private keys and create a certificate chain:
-
Enter an alias for the key pair.
-
Browse and select the private key file or provide the path.
-
Browse and select the client certificate file or provide the path.
-
Click Add Certificate to Chain (or Add More Certificate Paths).
-
Repeat the process until you have added the last certificate and key for this certificate chain.
-
Click Add New Client Certificate.
-
MC adds the resulting certificate chain to its list.
Adding a new certificate for the browser connection
You can view the existing TLS certificate for the browser connection to the MC server, or add a new certificate to replace it.
To view or replace the current SSL/TLS certificate that MC uses for the user's browser's HTTPS connection to the MC server:
-
From the MC home page, navigate to MC Settings > SSL/TLS Certificates.
The top pane displays the current certificate for the browser connection to the MC server, including the certificate's expiration date:
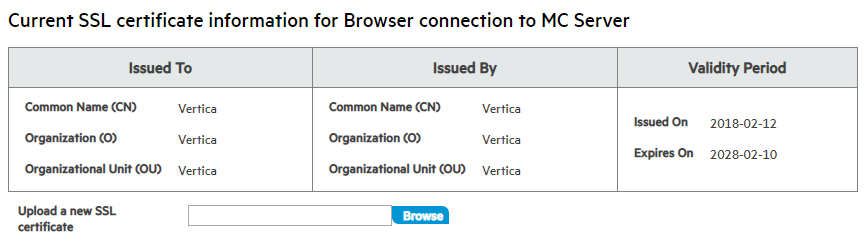
-
To replace the current certificate, click Browse next to the Upload a new SSL certificate field.
MC opens an explorer window.
-
Select the certificate file you wish to upload and click Open. The certificate file must be in PEM (Privacy-enhanced Email Message) format.
MC replaces the prior certificate with the new certificate.
10 - Managing TLS certificates in MC
MC maintains a secure list containing all the CA certificates, and the client certificates or certificate chains and their corresponding key files, that you have uploaded into MC.
MC maintains a secure list containing all the CA certificates, and the client certificates or certificate chains and their corresponding key files, that you have uploaded into MC.
To manage the certificates already uploaded to MC, navigate to Home > MC Settings > SSL/TLS Certificates. This screen controls the TLS security settings for all of MC.
The top pane displays information about the current TLS certificate used to secure the user's browser connection to the MC server. You can add a new certificate to replace it. See .

The middle and lower panes allow you to add and remove CA and client certificates in MC.
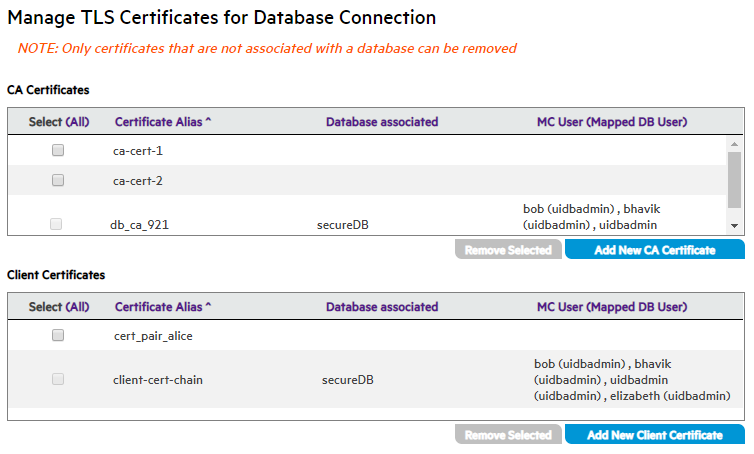
You can perform the following tasks to manage your TLS certificates and keys in MC.
For the security settings for a specific database, open the database in MC and navigate to Home > Databases and Clusters > DatabaseName > Settings and click the Security tab in the left navigation bar.
11 - Updating a TLS certificate in MC
When a TLS certificate is about to expire, has already expired, or otherwise becomes unusable, it needs to be updated.
When a TLS certificate is about to expire, has already expired, or otherwise becomes unusable, it needs to be updated.
This is the method for updating a certificate:
-
In MC, add the new certificate that will replace the expiring or invalid certificate. See Adding TLS certificates in MC.
Note
You can add and configure the new certificate for the database or user whose existing certificate is or will soon be invalid, as a single step, or two steps. Configuring the new certificate for the database dissociates the previously configured certificate from that database. See
Connecting securely from MC to a Vertica database.
-
After the old certificate has been disassociated from all databases and users, you can remove it from the MC. See Removing TLS certificates from MC.
12 - Removing TLS certificates from MC
In some cases, it may be appropriate to disable TLS for a database in MC.
In some cases, it may be appropriate to disable TLS for a database in MC. Disabling TLS for the database disassociates all the certificates configured for that database. For more information, see Enabling or disabling TLS for a database in MC.
Disassociating a certificate from a database in MC
Before you can remove a certificate from MC, you must be sure the certificate is not associated with (being used by) any databases. The MC administrator can disassociate a certificate from a database in MC using either of these methods:
Configuring a new certificate on the database in MC
When you configure a new certificate to serve a specific purpose on a database in MC, the new certificate replaces the old certificate. The newly configured certificate is now associated with the database, and the old certificate is no longer associated and can be removed.
Navigate to Databases and Clusters > DbName > Database Settings > Configure TLS.
For details, see Configuring TLS for a monitored database in MC
Removing the TLS configuration on the database
You can remove one or more TLS certificates from the MC, provided the certificates are not associated with a database. To remove a certificate:
-
From the MC home page, navigate to MC Settings > SSL/TLS Certificates.
-
In the Manage TLS Certificates for Database Connection section, locate the row or rows for one or more CA or client certificates you want to remove. This example shows only the CA Certificates pane:
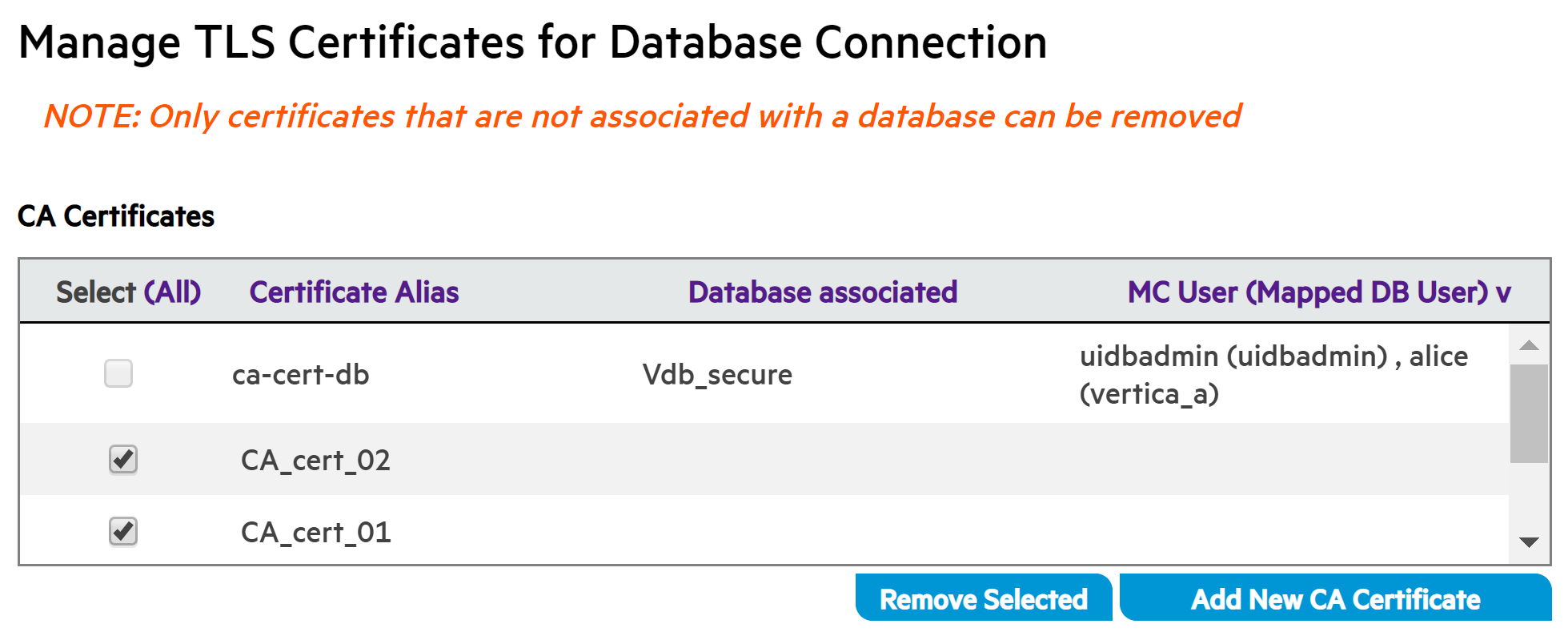
-
If the Database associated field is empty for that certificate, you can click to select the certificate for removal, and click Remove Selected. In the illustration above, CA_cert_02 and CA_cert_01 are selected for removal.
Note
If you remove one client certificate that is part of a certificate chain, MC removes the entire certificate chain.
14 - Bulk-configure a group of MC users for TLS
You as the MC administrator can create multiple MC users and map them all to the same database user id on the Vertica database server side.
You as the MC administrator can create multiple MC users and map them all to the same database user id on the Vertica database server side. You map the users in MC when you create them. For details, see User administration in MC.
You can then configure all the MC users that are mapped to a single Vertica database user id, to use the same client certificate or certificate chain and private key in MC, in a single bulk configuration process:
-
Navigate to MC Home > Databases and Clusters > DbName> Settings > Security.
-
Click Configure TLS Connection to launch the MC certificates wizard.
-
Complete steps 1 through 3 in the wizard to configure a CA certificate and the client certificate or certificate chain and key that you want to use for multiple MC users. For details, see MC certificates wizard.
-
After you complete these steps, the wizard displays the Apply TLS configuration to MC users mapped to database page as step 4 in the left wizard pane.
-
To apply the same CA certificate, client certificate and key you just configured to one or more additional users, click the check boxes for those users.
Note
All the users you select must be mapped to the same Vertica database user id.
-
To complete the configuration, click Review. MC displays a confirmation screen:
-
To complete the configuration of this CA certificate for the database and this client certificate/key pair for the selected MC users, click Configure TLS for DB.
-
MC confirms that the action was a success. Click Close to close the Certificate wizard.


